|
|
| Line 1: |
Line 1: |
| [[File:emacs-logo.png]]
| | == Open vSwitch == |
|
| |
|
| Emacs is a famous text editor, famous by its flexibility and extensibility. One manual describes it as "the extensible, customizable, self-documenting, real-time display editor".
| | Open vSwitch is a production quality, multilayer virtual switch licensed under the open source Apache 2.0 license. It is designed to enable massive network automation through programmatic extension, while still supporting standard management interfaces and protocols (e.g. NetFlow, sFlow, SPAN, RSPAN, CLI, LACP, 802.1ag). In addition, it is designed to support distribution across multiple physical servers similar to VMware's vNetwork distributed vswitch or Cisco's Nexus 1000V. |
|
| |
|
| This page is designed to give users a good place to share their config and settings for a nice emacs setup.
| | === Features === |
|
| |
|
| == installing emacs ==
| | The current stablerelease of Open vSwitch (version 1.4.0) supports the following features: |
|
| |
|
| <pre>
| | * Visibility into inter-VM communication via NetFlow, sFlow(R), SPAN, RSPAN, and GRE-tunneled mirrors |
| emerge -avt emacs
| | * LACP (IEEE 802.1AX-2008) |
| </pre>
| | * Standard 802.1Q VLAN model with trunking |
| | * A subset of 802.1ag CCM link monitoring |
| | * STP (IEEE 802.1D-1998) |
| | * Fine-grained min/max rate QoS |
| | * Support for HFSC qdisc |
| | * Per VM interface traffic policing |
| | * NIC bonding with source-MAC load balancing, active backup, and L4 hashing |
| | * OpenFlow protocol support (including many extensions for virtualization) |
| | * IPv6 support |
| | * Multiple tunneling protocols (Ethernet over GRE, CAPWAP, IPsec, GRE over IPsec) |
| | * Remote configuration protocol with local python bindings |
| | * Compatibility layer for the Linux bridging code |
| | * Kernel and user-space forwarding engine options |
| | * Multi-table forwarding pipeline with flow-caching engine |
| | * Forwarding layer abstraction to ease porting to new software and hardware platforms |
| | |
| | == Configuring Open vSwitch == |
|
| |
|
| for the standard gnu emacs and | | Open vSwitch needs to be compiled with the kernel modules (modules USE flag) for kernel versions <3.3, since 3.3.0 it is included in the kernel as a module named "Open vSwitch" and can be found in kernel at '''Networking Support -> Networking Options -> Open vSwitch'''. Then just emerge openvswitch with |
|
| |
|
| <pre> | | <pre> |
| emerge -avt xemacs | | # emerge -avt openvswitch |
| </pre> | | </pre> |
|
| |
|
| for the 1980 created fork of emacs, both should handle the same, while emacs on its own stands here for both. If you install additional extensions for both you might need to add <tt>app-emacs</tt> or <tt>app-xemacs</tt> to the package as there are two different versions for both.
| | == Using Open vSwitch == |
|
| |
|
| == What emacs is and what it is not ==
| | These Configs are taken from the Open vSwitch website at http://openvswitch.org and adjusted to funtoo's needs |
|
| |
|
| (X)Emacs is primarily a text editor and not a word processor, it concentrates on manipulating any kind of text, rather than manipulating the font and look. It is client and GUI based, so can be used on local box in graphical environments with a GUI and remote on a server in a client mode. (X)Emacs provides commands for manipulate every kind of text and syntax highlighting.
| | === VLANs === |
|
| |
|
| === Customizability === | | ==== Setup ==== |
|
| |
|
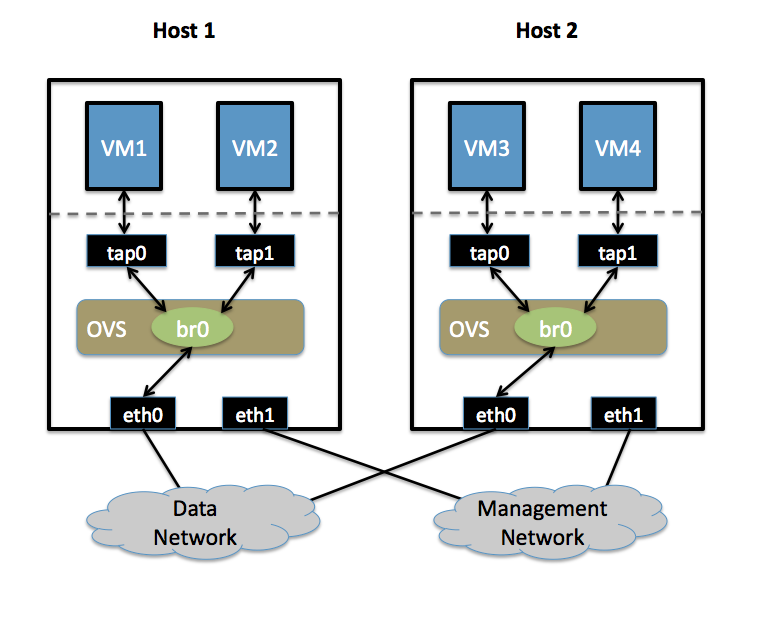
| (X)Emacs is highly customizable in many ways through: | | * Two Physical Networks |
| | ** Data Network: Eternet network for VM data traffic, which will carry VLAN tagged traffic between VMs. Your physical switch(es) must be capable of forwarding VLAN tagged traffic and the physical switch ports should be VLAN trunks (Usually this is default behavior. Configuring your physical switching hardware is beyond the scope of this document). |
| | ** Management Network: This network is not strictly required, but it is a simple way to give the physical host an IP address for remote access, since an IP address cannot be assigned directly to eth0. |
| | * Two Physical Hosts |
| | Host1, Host2. Both hosts are running Open vSwitch. Each host has two NICs: |
| | ** eth0 is connected to the Data Network. No IP address can be assigned on eth0 |
| | ** eth1 is connected to the Management Network (if necessary). eth1 has an IP address that is used to reach the physical host for management. |
| | * Four VMs |
| | VM1, VM2 run on Host1. VM3, VM4 run on Host2. |
| | Each VM has a single interface that appears as a Linux device (e.g., "tap0") on the physical host. (Note: for Xen/XenServer, VM interfaces appear as Linux devices with names like "vif1.0"). |
| | [[image:2host-4vm.png]] |
|
| |
|
| * the <tt>customize</tt> extension, which allows settings of customized variables, such as color themes, graphical interface, etc. This part is intended for emacs beginners, who do not want to work with Emacs lisp code.
| | ==== Goal ==== |
| * combine keystrokes to execute complex makros.
| |
| * using Emacs Lisp. Designed for the emacs professional.
| |
|
| |
|
| === Extensibility ===
| | Isolate VMs using VLANs on the Data Network. |
| | VLAN1: VM1, VM3 |
| | VLAN2: VM2, VM4 |
|
| |
|
| As a result of the above points, (X)Emacs behaviour can be easily definied to all text behavings without limit. Like some of the examples below show you:
| | ==== Configuration ==== |
| | Perform the following configuration on Host1: |
| | # Create an OVS bridge <pre>ovs-vsctl add-br br0</pre> |
| | # Add eth0 to the bridge (by default, all OVS ports are VLAN trunks, so eth0 will pass all VLANs) <pre>ovs-vsctl add-port br0 eth0</pre> |
| | # Add VM1 as an "access port" on VLAN1 <pre>ovs-vsctl add-port br0 tap0 tag=1</pre> |
| | # Add VM2 on VLAN2 <pre>ovs-vsctl add-port br0 tap0 tag=2</pre> |
| | On Host2, repeat the same configuration to setup a bridge with eth0 as a trunk <pre>ovs-vsctl add-br br0 |
| | ovs-vsctl add-port br0 eth0</pre> |
| | # Add VM3 to VLAN1 <pre>ovs-vsctl add-port br0 tap0 tag=1</pre> |
| | # Add VM4 to VLAN2 <pre>ovs-vsctl add-port br0 tap0 tag=2</pre> |
|
| |
|
| * AUCTeX, A suite for LaTeX and other TeX versions, | | === sFlow === |
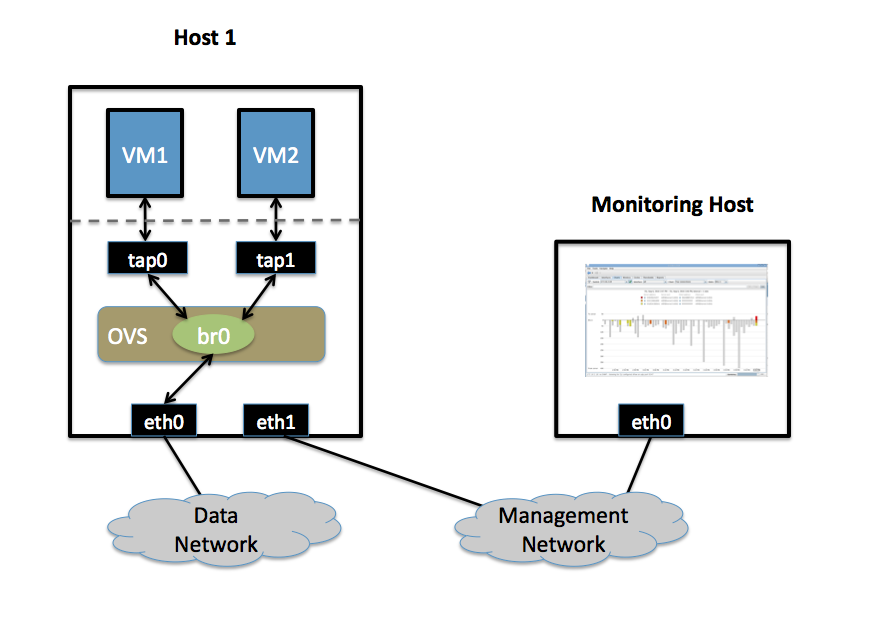
| * ERC, A Emacs IRC client, | | This will setup a VM traffic Monitor using sFlow. |
| * ORG-mode, A Emacs PIM and Orga tool | | ==== Setup ==== |
| * Wanderlust, A highly flexible Mail tool for Emacs | | * Two Physical Networks |
| | ** Data Network: Eternet network for VM data traffic. |
| | ** Management Network: This network must exist, as it is used to send sFlow data from the agent to the remote collector. |
| | * Two Physical Hosts |
| | ** Host1 runs Open vSwitch and has two NICs: |
| | *** eth0 is connected to the Data Network. No IP address can be assigned on eth0. |
| | *** eth1 is connected to the Management Network. eth1 has an IP address for management traffic (including sFlow). |
| | ** Monitoring Host can be any computer that run the sFlow collector. Here we use [http://www.inmon.com/products/sFlowTrend.php sFlowTrend], a free sFlow collector, a simple cross-platform Java tool. Other sFlow collectors should work equally well. |
| | *** eth0 is connected to the Management Netowrk: eth0 has an IP address that can reach Host1. |
| | * Two VMs |
| | VM1, VM2 run on Host1. Each VM has a single interface that appears as a Linux device (e.g., "tap0") on the physical host. (Note: same for Xen/XenServer as in the VLANs section.) |
| | [[image:sflow-setup.png]] |
|
| |
|
| == User Configs == | | ==== Goal ==== |
| === golodhrim's config === | | Monitor traffic sent to/from VM1 and VM2 on the Data network using an sFlow collector. |
| ==== .emacs ====
| |
|
| |
|
| | ==== Configuration ==== |
| | Define the following configuration values in your shell environment. The default port for sFlowTrend is 6343. You will want to set your own IP address for the collector in the place of 10.0.0.1. Setting the AGENT_IP value to eth1 indicates that the sFlow agent should send traffic from eth1's IP address. The other values indicate settings regarding the frequency and type of packet sampling that sFlow should perform. |
| | <pre> |
| | # export COLLECTOR_IP=10.0.0.1 |
| | # export COLLECTOR_PORT=6343 |
| | # export AGENT_IP=eth1 |
| | # export HEADER_BYTES=128 |
| | # export SAMPLING_N=64 |
| | # export POLLING_SECS=10 |
| | </pre> |
| | Run the following command to create an sFlow configuration and attach it to bridge br0: |
| <pre> | | <pre> |
| ;;;;;;;;;;;;;;;;;;;;;;
| | ovs-vsctl -- -id=@sflow create sflow agent=${AGENT_IP} target=\”${COLLECTOR_IP}:${COLLECTOR_PORT}\” header=${HEADER_BYTES} sampling=${SAMPLING_N} polling=${POLLING_SECS} — set bridge br0 sflow=@sflow |
| ;; General Settings ;;
| |
| ;;;;;;;;;;;;;;;;;;;;;;
| |
| | |
| (setq emacs-root-dir (concat (getenv "HOME") "/em/"))
| |
| | |
| (setq inhibit-startup-message t) ;; Suppress the startup message
| |
| (setq standard-indent 4) ;; Default indent level is 3 chars
| |
| (setq-default indent-tabs-mode nil) ;; Indent with spaces, not tabs
| |
| | |
| (setq make-backup-files nil) ;; Enable backup files.
| |
| (setq version-control nil) ;; Enable versioning with default values
| |
| (setq backup-directory-alist (quote ((".*" . "~/.emacs_backups/")))) ;; Save all backup file in this directory.
| |
| | |
| (line-number-mode 1) ;; Show line-number in the mode line
| |
| (column-number-mode 1) ;; Show column-number in the mode line
| |
| | |
| (setq auto-fill-mode 1) ;; Line wrap
| |
| | |
| (set-default-font "Inconsolata-12")
| |
| | |
| (setq browse-url-browser-function 'browse-url-generic
| |
| browse-url-generic-program "google-chrome")
| |
| | |
| (global-set-key (kbd "C-<prior>") 'previous-buffer)
| |
| (global-set-key (kbd "C-<next>" ) 'next-buffer )
| |
| | |
| | |
| (setq load-path (cons "~/.emacs.d/plugins" load-path))
| |
| | |
| (setq global-font-lock-mode 1)
| |
| | |
| (show-paren-mode 1)
| |
| | |
| ;;;;;;;;;;;;;;;;;;
| |
| ;; el-get setup ;;
| |
| ;;;;;;;;;;;;;;;;;;
| |
| (add-to-list 'load-path "~/.emacs.d/el-get/el-get")
| |
| (unless (require 'el-get nil t)
| |
| (with-current-buffer
| |
| (url-retrieve-synchronously "https://raw.github.com/golodhrim/el-get/master/el-get-install.el")
| |
| (end-of-buffer)
| |
| (eval-print-last-sexp)))
| |
| | |
| (el-get 'sync)
| |
| | |
| ;;;;;;;;;;;;;;;
| |
| ;; mediawiki ;;
| |
| ;;;;;;;;;;;;;;;
| |
| (require 'mediawiki)
| |
| | |
| ;;;;;;;;;;;;;;;;;;;;
| |
| ;; Org-mode stuff ;;
| |
| ;;;;;;;;;;;;;;;;;;;;
| |
| | |
| ;; Tell emacs where org-mode is
| |
| ;;(setq load-path (cons "/usr/share/emacs/site-lisp/org-mode/" load-path))
| |
| ;;(setq load-path (cons "/usr/share/emacs/site-lisp/org-mode/contrib/" load-path))
| |
| (require 'org-install) ;; Tell emacs to use org-mode
| |
| (add-to-list 'auto-mode-alist '("\\.org$" . org-mode)) ;; Turn on org-mode for all *.org files
| |
| | |
| ;; Some key sequences
| |
| (define-key global-map "\C-cl" 'org-store-link)
| |
| (define-key global-map "\C-ca" 'org-agenda)
| |
| (global-set-key [f9] 'org-archive-subtree-default)
| |
| | |
| (setq org-log-done t) ;; I have no idea what this does, it was in the manual -- think it controls whether or not to log time completed for tasks
| |
| | |
| (setq org-directory "~/notes")
| |
| | |
| ;; Files that should be included in agenda views:
| |
| (setq org-agenda-files (list "~/notes/business.org"
| |
| "~/notes/personal.org"
| |
| "~/notes/projects/"
| |
| "~/notes/projects/writing/"))
| |
| | |
| (setq org-todo-keywords '((type "TODO" "Postponed" "Upcoming" "Doing" "|" "DONE(#)"))) ;; TODO workflows
| |
| | |
| (setq org-tag-alist '(("work" . ?k) ("personal" . ?p) ("organization" . ?o) ("writing" . ?w) ("code" . ?c) ("blog" . ?b) ("funtoo" . ?f) ("social" . ?s))) ;; Most-used tags, with shortcuts
| |
| | |
| ;; Capture stuff
| |
| (setq org-default-notes-file "~/.org/capture.org")
| |
| (define-key global-map "\C-cc" 'org-capture)
| |
| (setq org-refile-targets '((org-agenda-files :level . 1)(org-agenda-files :level . 2)))
| |
| (setq org-refile-use-outline-path 'file)
| |
| | |
| (setq org-capture-templates
| |
| '(("t" "Todo" entry (file+headline "~/.org/capture.org" "Tasks")
| |
| "- TODO %?\n %i\n %a")
| |
| ("j" "Journal" entry (file+datetree "~/.org/journal.org")
| |
| "- %?\nEntered on %U\n %i\n %a")))
| |
| | |
| (setq org-mobile-directory "~/Dropbox/MobileOrg")
| |
| (setq org-mobile-use-encryption)
| |
| (setq org-mobile-use-encryption-password "PASSWORD")
| |
| (setq org-mobile-inbox-for-pull "~/notes/mobileorg/inbox.org")
| |
| | |
| ;;;;;;;;;;;;;;;;;;;
| |
| ;; Markdown Mode ;;
| |
| ;;;;;;;;;;;;;;;;;;;
| |
| | |
| (require 'markdown-mode)
| |
| (add-to-list 'auto-mode-alist '("\\.markdown$" . markdown-mode))
| |
| (add-to-list 'auto-mode-alist '("\\.md$" . markdown-mode))
| |
| | |
| ;;;;;;;;;;;;;;;;
| |
| ;; Python IDE ;;
| |
| ;;;;;;;;;;;;;;;;
| |
| (c-add-style
| |
| "python-new"
| |
| '((indent-tabs-mode . nil)
| |
| (fill-column . 78)
| |
| (c-basic-offset . 4)
| |
| (c-offsets-alist . ((substatement-open . 0)
| |
| (inextern-lang . 0)
| |
| (arglist-intro . +)
| |
| (knr-argdecl-intro . +)))
| |
| (c-hanging-braces-alist . ((brace-list-open)
| |
| (brace-list-intro)
| |
| (brace-list-close)
| |
| (brace-entry-open)
| |
| (substatement-open after)
| |
| (block-close . c-snug-do-while)))
| |
| (c-block-comment-prefix . "* "))
| |
| )
| |
| | |
| ;; This is a very crude hook that auto-selects the C style depending on
| |
| ;; whether it finds a line starting with tab in the first 3000 characters
| |
| ;; in the file
| |
| (defun c-select-style ()
| |
| (save-excursion
| |
| (if (re-search-forward "^\t" 3000 t)
| |
| (c-set-style "python")
| |
| (c-set-style "python-new"))))
| |
| (add-hook 'c-mode-hook 'c-select-style)
| |
| | |
| ;;;;;;;;;;;;
| |
| ;; Django ;;
| |
| ;;;;;;;;;;;;
| |
| (yas/initialize)
| |
| (add-to-list 'load-path "~/.emacs.d/el-get/django-mode/")
| |
| (require 'django-html-mode)
| |
| (require 'django-mode)
| |
| (yas/load-directory "~/.emacs.d/el-get/django-mode/snippets")
| |
| (add-to-list 'auto-mode-alist '("\\.djhtml$" . django-html-mode))
| |
| | |
| ;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;
| |
| ;; Document Engineering (AUCTeX + ConTeXt) ;;
| |
| ;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;;
| |
| (load "auctex.el" nil t t)
| |
| (load "preview-latex.el" nil t t)
| |
| | |
| (setq TeX-auto-save 1)
| |
| (setq TeX-parse-self 1)
| |
| (setq TeX-auto-untabify 1)
| |
| (setq TeX-display-help 1)
| |
| (setq TeX-save-query nil)
| |
| (setq TeX-clean-confirm nil)
| |
| (setq-default TeX-master nil)
| |
| | |
| (add-hook 'TeX-mode-hook (lambda () (TeX-fold-mode 1)))
| |
| (add-hook 'TeX-mode-hook (lambda () (TeX-source-specials-mode 1)))
| |
| (add-hook 'TeX-mode-hook (lambda () (TeX-toggle-debug-bad-boxes)))
| |
| (add-hook 'TeX-mode-hook (lambda () (TeX-toggle-debug-warnings)))
| |
| (add-hook 'TeX-mode-hook (lambda () (outline-minor-mode)))
| |
| (add-hook 'TeX-mode-hook (lambda () (abbrev-mode t)))
| |
| (add-hook 'TeX-mode-hook (lambda () (auto-fill-mode 1)))
| |
| | |
| (add-hook 'TeX-mode-hook 'LaTeX-math-mode)
| |
| | |
| (autoload 'etexshow "etexshow" "Browser for ConTeXt commands." t)
| |
| | |
| (setq etexshow-xml-files-alist
| |
| `((,(concat emacs-root-dir "libs/etexshow/cont-en.xml") .
| |
| ,(concat "/tmp/cont-en.cache"))))
| |
| | |
| (setq etexshow-comment-file
| |
| (concat emacs-root-dir "libs/etexshow/cont-en-comments.xml"))
| |
| | |
| (setq TeX-PDF-mode 1)
| |
| (setq revert-without-query '(".+pdf$"))
| |
| (add-hook 'doc-view-mode-hook 'auto-revert-mode)
| |
| | |
| ;;;;;;;;;;
| |
| ;; bbdb ;;
| |
| ;;;;;;;;;;
| |
| (setq bbdb-file "~/.emacs.d/.bbdb")
| |
| (require 'bbdb)
| |
| (bbdb-initialize)
| |
| (setq
| |
| bbdb-offer-save 1 ;; 1 means save-without-asking
| |
| bbdb-use-pop-up t ;; allow popups for addresses
| |
| bbdb-electric-p t ;; be disposable with SPC
| |
| bbdb-popup-target-lines 1 ;; very small
| |
| bbdb-dwim-net-address-allow-redundancy t ;; always use full name
| |
| bbdb-quiet-about-name-mismatches 2 ;; show name-mismatches 2 secs
| |
| bbdb-always-add-address t ;; add new addresses to existing...
| |
| ;; ...contacts automatically
| |
| bbdb-canonicalize-redundant-nets-p t ;; x@foo.bar.cx => x@bar.cx
| |
| bbdb-completion-type nil ;; complete on anything
| |
| bbdb-complete-name-allow-cycling t ;; cycle through matches
| |
| ;; this only works partially
| |
| bbdb-message-caching-enabled t ;; be fast
| |
| bbdb-use-alternate-names t ;; use AKA
| |
| bbdb-elided-display t ;; single-line addresses
| |
| ;; auto-create addresses from mail
| |
| bbdb/mail-auto-create-p 'bbdb-ignore-some-messages-hook
| |
| bbdb-ignore-some-messages-alist ;; don't ask about fake addresses
| |
| ;; NOTE: there can be only one entry per header (such as To, From)
| |
| ;; http://flex.ee.uec.ac.jp/texi/bbdb/bbdb_11.html
| |
| '(( "From" . "no.?reply\\|DAEMON\\|daemon\\|facebookmail\\|twitter")))
| |
| | |
| ;;;;;;;;;;;;;;;;;
| |
| ;; Jabber Mode ;;
| |
| ;;;;;;;;;;;;;;;;;
| |
| | |
| (require 'jabber-autoloads)
| |
| (setq jabber-account-list '(
| |
| ("USER@jabber-server.tld"
| |
| (:password . "PASSWORD")
| |
| )
| |
| )
| |
| )
| |
| (setq
| |
| jabber-history-enabled t
| |
| jabber-use-global-history nil
| |
| jabber-backlog-number 40
| |
| jabber-backlog-days 30
| |
| )
| |
| | |
| (add-hook 'jabber-chat-mode-hook 'goto-address)
| |
| | |
| (load "~/.emacs.d/plugins/autosmiley.el")
| |
| (require 'autosmiley)
| |
| (add-hook 'jabber-chat-mode-hook 'autosmiley-mode)
| |
| | |
| (defvar libnotify-program "/usr/bin/notify-send")
| |
| | |
| (defun notify-send (title message)
| |
| (start-process "notify" " notify"
| |
| libnotify-program "--expire-time=4000" title message))
| |
| | |
| (defun libnotify-jabber-notify (from buf text proposed-alert)
| |
| "(jabber.el hook) Notify of new Jabber chat messages via libnotify"
| |
| (when (or jabber-message-alert-same-buffer
| |
| (not (memq (selected-window) (get-buffer-window-list buf))))
| |
| (if (jabber-muc-sender-p from)
| |
| (notify-send (format "(PM) %s"
| |
| (jabber-jid-displayname (jabber-jid-user from)))
| |
| (format "%s: %s" (jabber-jid-resource from) text)))
| |
| (notify-send (format "%s" (jabber-jid-displayname from))
| |
| text)))
| |
| | |
| (add-hook 'jabber-alert-message-hooks 'libnotify-jabber-notify)
| |
| | |
| (defun jabber-visit-history (jid)
| |
| "Visit jabber history with JID in a new buffer.
| |
| | |
| Performs well only for small files. Expect to wait a few seconds
| |
| for large histories. Adapted from `jabber-chat-create-buffer'."
| |
| (interactive (list (jabber-read-jid-completing "JID: ")))
| |
| (let ((buffer (generate-new-buffer (format "*-jabber-history-%s-*"
| |
| (jabber-jid-displayname jid)))))
| |
| (switch-to-buffer buffer)
| |
| (make-local-variable 'jabber-chat-ewoc)
| |
| (setq jabber-chat-ewoc (ewoc-create #'jabber-chat-pp))
| |
| (mapc 'jabber-chat-insert-backlog-entry
| |
| (nreverse (jabber-history-query nil nil t t "."
| |
| (jabber-history-filename jid))))
| |
| (view-mode)))
| |
| | |
| ;;;;;;;;;;
| |
| ;; EMMS ;;
| |
| ;;;;;;;;;;
| |
| (require 'emms-setup)
| |
| (emms-devel)
| |
| (emms-default-players)
| |
| | |
| ;;;;;;;;;
| |
| ;; ERC ;;
| |
| ;;;;;;;;;
| |
| (require 'erc)
| |
| (require 'erc-extension)
| |
| (require 'erc-services)
| |
| (require 'erc-tex)
| |
| (require 'tls)
| |
| (require 'erc-nicklist)
| |
| | |
| (and
| |
| (require 'erc-highlight-nicknames)
| |
| (add-to-list 'erc-modules 'highlight-nicknames)
| |
| (erc-update-modules))
| |
| | |
| (erc-services-mode 1)
| |
| | |
| (setq tls-program '("openssl s_client -connect %h:%p -no_ssl2 -ign_eof
| |
| -CAfile /home/USER/.ssl/USER.pem
| |
| -cert /home/USER/.ssl/USER.pem"
| |
| "gnutls-cli --priority secure256
| |
| --x509cafile /home/USER/.ssl/USER.pem
| |
| --x509certfile /home/USER/.ssl/USER.pem -p %p %h"
| |
| "gnutls-cli --priority secure256 -p %p %h"))
| |
| | |
| (autoload 'erc-nick-notify-mode "erc-nick-notify" "Minor mode that calls `erc-nick-notify-cmd' when his nick gets mentioned in an erc channel" t)
| |
| (eval-after-load 'erc '(erc-nick-notify-mode t))
| |
| (defun irc-erc ()
| |
| "Fire up IRC."
| |
| (interactive)
| |
| (erc-tls :server "chat.freenode.net" :port 7000 :nick "USER" :full-name "FULL NAME" :password "PASSWORD"))
| |
| | |
| (setq erc-autojoin-channels-alist '(("freenode.net" "#frogandowl" "#funtoo" "#funtoo-quebec" "#syntazia" "#context" "#nginx" "#emacs" "#openvswitch")))
| |
| (setq erc-log-channels-directory "~/.erc/logs/")
| |
| (setq erc-log-insert-log-on-open nil)
| |
| (setq erc-save-buffer-on-part nil
| |
| erc-save-buffer-queries-on-quit nil
| |
| erc-log-write-after-send t
| |
| erc-log-write-after-insert t)
| |
| | |
| (require 'smiley)
| |
| (add-to-list 'smiley-regexp-alist '("\\(:-?]\\)\\W" 1 "forced"))
| |
| (add-to-list 'smiley-regexp-alist '("\\s-\\(:-?/\\)\\W" 1 "wry"))
| |
| (add-to-list 'smiley-regexp-alist '("\\(:-?(\\)\\W" 1 "sad"))
| |
| (add-to-list 'smiley-regexp-alist '("\\((-?:\\)\\W" 1 "reverse-smile"))
| |
| (add-to-list 'smiley-regexp-alist '("\\(:-?D\\)\\W" 1 "grin"))
| |
| (add-to-list 'smiley-regexp-alist '("\\(:-?P\\)\\W" 1 "poke"))
| |
| | |
| ;; (setq smiley-cached-regexp-alist nil)
| |
| ;; (smiley-update-cache)
| |
| | |
| ;;;;;;;;;;;;;;;;
| |
| ;; Wanderlust ;;
| |
| ;;;;;;;;;;;;;;;;
| |
| (autoload 'wl "wl" "Wanderlust" t)
| |
| | |
| ;;;;;;;;;;;;;;;
| |
| ;; mailcrypt ;;
| |
| ;;;;;;;;;;;;;;;
| |
| (require 'mailcrypt)
| |
| (add-hook 'wl-summary-mode-hook 'mc-install-read-mode)
| |
| (add-hook 'wl-mail-setup-hook 'mc-install-write-mode)
| |
| | |
| (defun mc-wl-verify-signature ()
| |
| (interactive)
| |
| (save-window-excursion
| |
| (wl-summary-jump-to-current-message)
| |
| (mc-verify)))
| |
| | |
| (defun mc-wl-decrypt-message ()
| |
| (interactive)
| |
| (save-window-excursion
| |
| (wl-summary-jump-to-current-message)
| |
| (let ((inhibit-read-only t))
| |
| (mc-decrypt))))
| |
| | |
| (eval-after-load "mailcrypt"
| |
| '(setq mc-modes-alist
| |
| (append
| |
| (quote
| |
| ((wl-draft-mode (encrypt . mc-encrypt-message)
| |
| (sign . mc-sign-message))
| |
| (wl-summary-mode (decrypt . mc-wl-decrypt-message)
| |
| (verify . mc-wl-verify-signature))))
| |
| mc-modes-alist)))
| |
| | |
| ;;;;;;;;;;;;;;;;;;;;;
| |
| ;; notify function ;;
| |
| ;;;;;;;;;;;;;;;;;;;;;
| |
| (defun djcb-popup (title msg &optional icon sound)
| |
| "Show a popup if we're on X, or echo it otherwise; TITLE is the title of the message, MSG is the context. Optionally, you can provide an ICON and a sound to be played"
| |
| (interactive)
| |
| (when sound (shell-command
| |
| (concat "mplayer2 -really-quiet " sound " 2> /dev/null")))
| |
| (if (eq window-system 'x)
| |
| (shell-command (concat "notify-send "
| |
|
| |
| (if icon (concat "-i " icon) "")
| |
| " '" title "' '" msg "'"))
| |
| ;; text only version
| |
| (message (concat title ": " msg))))
| |
| | |
| ;; the appointment notification facility
| |
| (setq
| |
| appt-message-warning-time 15 ;; warn 15 min in advance
| |
| appt-display-mode-line t ;; show in the modeline
| |
| appt-display-format 'window) ;; usr our func
| |
| (appt-activate t) ;; active appt (appointment notification)
| |
| (display-time)
| |
| | |
| ;; update appt each time agenda opened
| |
| (add-hook 'org-finalize-agenda-hook 'org-agenda-to-appt)
| |
| | |
| ;; our little facade-function for djcb-popup
| |
| (defun djcb-appt-display (min-to-app new-time msg)
| |
| (djcb-popup (format "Appointment in %s minute(s)" min-to-app) msg
| |
| "/usr/share/icons/gnome/32x32/status/appointment-soon.png"
| |
| "/usr/share/sounds/purple/alert.wav"))
| |
| (setq appt-disp-window-function (function djcb-appt-display))
| |
| | |
| ;;;;;;;;;;;;;;;;;;;;;;;;;;
| |
| ;; Custom Variable sets ;;
| |
| ;;;;;;;;;;;;;;;;;;;;;;;;;;
| |
| (custom-set-variables
| |
| ;; custom-set-variables was added by Custom.
| |
| ;; If you edit it by hand, you could mess it up, so be careful.
| |
| ;; Your init file should contain only one such instance.
| |
| ;; If there is more than one, they won't work right.
| |
| '(TeX-command-list (quote (("TeX" "%(PDF)%(tex) %`%S%(PDFout)%(mode)%' %t" TeX-run-TeX nil (plain-tex-mode texinfo-mode ams-tex-mode) :help "Run plain TeX") ("LaTeX" "%`%l%(mode)%' %t" TeX-run-TeX nil (latex-mode doctex-mode) :help "Run LaTeX") ("Makeinfo" "makeinfo %t" TeX-run-compile nil (texinfo-mode) :help "Run Makeinfo with Info output") ("Makeinfo HTML" "makeinfo --html %t" TeX-run-compile nil (texinfo-mode) :help "Run Makeinfo with HTML output") ("AmSTeX" "%(PDF)amstex %`%S%(PDFout)%(mode)%' %t" TeX-run-TeX nil (ams-tex-mode) :help "Run AMSTeX") ("ConTeXt MKIV" "context %t" TeX-run-TeX nil (context-mode) :help "Run ConTeXt MKIV") ("ConTeXt" "texexec --once --texutil %(execopts)%t" TeX-run-TeX nil (context-mode) :help "Run ConTeXt once") ("ConTeXt Full" "texexec %(execopts)%t" TeX-run-TeX nil (context-mode) :help "Run ConTeXt until completion") ("BibTeX" "bibtex %s" TeX-run-BibTeX nil t :help "Run BibTeX") ("View" "%V" TeX-run-discard-or-function t t :help "Run Viewer") ("Print" "%p" TeX-run-command t t :help "Print the file") ("Queue" "%q" TeX-run-background nil t :help "View the printer queue" :visible TeX-queue-command) ("File" "%(o?)dvips %d -o %f " TeX-run-command t t :help "Generate PostScript file") ("Index" "makeindex %s" TeX-run-command nil t :help "Create index file") ("Check" "lacheck %s" TeX-run-compile nil (latex-mode) :help "Check LaTeX file for correctness") ("Spell" "(TeX-ispell-document \"\")" TeX-run-function nil t :help "Spell-check the document") ("Clean" "TeX-clean" TeX-run-function nil t :help "Delete generated intermediate files") ("Clean All" "(TeX-clean t)" TeX-run-function nil t :help "Delete generated intermediate and output files") ("Other" "" TeX-run-command t t :help "Run an arbitrary command"))))
| |
| '(column-number-mode t)
| |
| '(erc-modules (quote (autojoin bbdb button completion fill irccontrols list log match menu move-to-prompt netsplit networks noncommands readonly ring services smiley stamp spelling track)))
| |
| '(mediawiki-site-alist (quote (("Funtoo" "http://www.funtoo.org/" "USER" "PASSWORD" "")))))
| |
| (custom-set-faces
| |
| ;; custom-set-faces was added by Custom.
| |
| ;; If you edit it by hand, you could mess it up, so be careful.
| |
| ;; Your init file should contain only one such instance.
| |
| ;; If there is more than one, they won't work right.
| |
| )
| |
| | |
| ;;;;;;;;;;;;;;;;;;
| |
| ;; Color-Themes ;;
| |
| ;;;;;;;;;;;;;;;;;;
| |
| ;;(add-to-list 'load-path "/usr/share/emacs/site-lisp/color-theme/color-theme.el")
| |
| ;;(add-to-list 'load-path "~/.emacs.d/themes/")
| |
| (require 'color-theme)
| |
| (color-theme-initialize)
| |
| ;;(color-theme-subtle-hacker)
| |
| (color-theme-twilight)
| |
| ;;(eval-after-load "color-theme"
| |
| ;; '(progn
| |
| ;; (color-theme-initialize)
| |
| ;; (require 'color-theme-citrus)
| |
| ;; (require 'color-theme-candy)
| |
| ;; (require 'color-theme-autumn-leaves)
| |
| ;; (require 'color-theme-inthedark)
| |
| ;; (require 'color-theme-marine)
| |
| ;; (require 'color-theme-october)
| |
| ;; (require 'color-theme-eatyourgreens)
| |
| ;; (require 'color-theme-august)
| |
| ;; (require 'color-theme-saddle-2)
| |
| ;; (color-theme-saddle-2)))
| |
| ;; (color-theme-subtle-hacker)))
| |
| | |
| (setq css-indent-offset 2)
| |
| </pre> | | </pre> |
| | | That is all. To configure sFlow on additional bridges, just replace "br0" in the above command with a different bridge name. |
| ==== .wl ====
| | To remove sFlow configuration from a bridge (in this case, 'br0'), run: |
| | |
| <pre> | | <pre> |
| ;; load bbdb support
| | ovs-vsctl remove bridge br0 sflow $SFLOWUUID |
| (require 'bbdb-wl)
| |
| (bbdb-wl-setup)
| |
| | |
| ;; setup from where to get addresses
| |
| (setq bbdb-wl-folder-regexp "^\.INBOX|^\.inbox|^\.Sent|^\.sent|^\.\[IMAPS\]\\Sent")
| |
| | |
| ;; define keybinding
| |
| (define-key wl-draft-mode-map (kbd "<C-tab>") 'bbdb-complete-name)
| |
| | |
| ;; set multiple e-mail addresses
| |
| (setq wl-user-mail-address-list (quote ("User@googlemail.com" "USER@own-server.tld")))
| |
| | |
| ;; handle ("d") mark
| |
| ;; remove = instant removal (same as "D"), thrash = move to wl-trash-folder
| |
| ;; string = move to string
| |
| (setq wl-dispose-folder-alist
| |
| '(
| |
| ("\.\*googlemail\\.com" "%[Imap]/Trash:"User@googlemail.com"/clear@imap.gmail.com:993!")
| |
| ("\.\*@own\-\server\\.tld" "%INBOX.Trash:"USER"/clear@imap.own-server.tld")
| |
| ))
| |
| | |
| ;; notify hook
| |
| (add-hook 'wl-biff-notify-hook
| |
| (lambda()
| |
| (djcb-popup "Wanderlust" "You have new mail!"
| |
| "/usr/share/icons/gnome/32x32/status/mail-unread.png"
| |
| "/usr/share/sounds/purple/alert.wav")))
| |
| | |
| ;; timer settings
| |
| (setq
| |
| wl-biff-check-interval 30 ;; check every 30 seconds
| |
| wl-biff-use-idle-timer t) ;; in the background
| |
| | |
| ;; Name of top-folder, default "Desktop"
| |
| (setq wl-folder-desktop-name "e-Mail")
| |
| | |
| ;; select correct email address when we _start_ writing a draft.
| |
| (add-hook 'wl-mail-setup-hook 'wl-draft-config-exec)
| |
| | |
| (setq wl-draft-config-alist
| |
| '(
| |
| ((string-match "googlemail.com" wl-draft-parent-folder)
| |
| (template . "User"))
| |
| ((string-match "own-server.tld" wl-draft-parent-folder)
| |
| (template . "USER"))
| |
| ))
| |
| | |
| ;; choose template with C-c C-j
| |
| (setq wl-template-alist
| |
| '(("User"
| |
| (wl-from . "Full Name <User@googlemail.com>")
| |
| ("From" . wl-from)
| |
| (wl-smtp-posting-user . "User")
| |
| (wl-smtp-posting-server . "smtp.gmail.com")
| |
| (wl-smtp-authenticate-type . "plain")
| |
| (wl-smtp-connection-type . 'starttls)
| |
| (wl-smtp-posting-port . 587)
| |
| (wl-local-domain . "googlemail.com")
| |
| (wl-message-id-domain . "smtp.gmail.com")
| |
|
| |
| (wl-fcc . "%[IMAPS]/Sent:\"User@googlemail.com\"/clear@imap.gmail.com:993!")
| |
| (wl-draft-folder . "%[IMAPS]/Draft:\"User@googlemail.com\"/clear@imap.gmail.com:993!")
| |
| )
| |
| ("USER"
| |
| (wl-from . "Full Name <USER@own-server.tld>")
| |
| ("From" . wl-from)
| |
| (wl-smtp-posting-user . "USER")
| |
| (wl-smtp-posting-server . "smtp.own-server.tld")
| |
| (wl-local-domain . "own-server.tld")
| |
|
| |
| (wl-fcc "%INBOX.Sent:USER/digest-md5@imap.own-server.tld:143")
| |
| (wl-draft-folder "%INBOX.Drafts:USER/digest-md5@imap.own-server.tld:143")
| |
| )
| |
| )
| |
| )
| |
| | |
| (define-key wl-template-mode-map (kbd "<right>") 'wl-template-next)
| |
| (define-key wl-template-mode-map (kbd "<left>") 'wl-template-prev)
| |
| | |
| (setq wl-default-spec "%")
| |
| | |
| (setq wl-fcc-force-as-read t)
| |
| (setq wl-auto-save-drafts-interval nil)
| |
| </pre> | | </pre> |
| | | To see all current sets of sFlow configuration parameters, run: |
| ==== .folders ====
| |
| | |
| <pre> | | <pre> |
| User@googlemail{
| | ovs-vsctl list sflow |
| %INBOX:"User@googlemail.com"/clear@imap.gmail.com:993! "Inbox"
| |
| [IMAPS-gmail]{
| |
| %[IMAPS]/Sent:"User@googlemail.com"/clear@imap.gmail.com:993! "Sent"
| |
| %[IMAPS]/Draft:"User@googlemail.com"/clear@imap.gmail.com:993! "Draft"
| |
| %[IMAPS]/Spam:"User@googlemail.com"/clear@imap.gmail.com:993! "Spam"
| |
| %[IMAPS]/Trash:"User@googlemail.com"/clear@imap.gmail.com:993! "Trash"
| |
| }
| |
| }
| |
| USER@own-server.tld{
| |
| %INBOX:USER/digest-md5@imap.own-server.tld "Inbox"
| |
| %INBOX.Sent:USER/digest-md5@imap.own-server.tld "Sent"
| |
| %INBOX.Drafts:USER/digest-md5@imap.own-server.tld "Drafts"
| |
| }
| |
| </pre> | | </pre> |
|
| |
|
| [[Category:HOWTO]]
| | === QoS Rate-limiting === |
| [[Category:Featured]]
| |