Difference between pages "Package:Nftables" and "Package:AMD Catalyst Video Drivers"
| Line 1: | Line 1: | ||
{{Ebuild | {{Ebuild | ||
|Summary= | |Summary=Accelerated ATI/AMD binary drivers for Radeon HD 5000 and newer chipsets. | ||
|CatPkg= | |CatPkg=x11-drivers/ati-drivers | ||
|Repository= | |Maintainer=Drobbins | ||
|Homepage= | |||
|Repository=Funtoo Overlay | |||
|Overlay=Funtoo | |||
}} | }} | ||
{{Important|Version 14.12-r3 and above now include ATI GLESv2 and EGL libraries, which should improve stabilty with GNOME.}} | |||
<tt>x11-drivers/ati-drivers</tt> (often referred to as "<tt>fglrx</tt>", the name of its kernel module) is the proprietary, accelerated driver for AMD (ATI) graphics cards. | |||
=== Preparing to Install === | |||
=== | ==== Default Kernel ==== | ||
If you are using the default kernel -- one like debian-sources that was built automatically, then you'll want to blacklist a few modules to prevent them from loading and interfering with the AMD Catalyst module. To avoid having the open source Radeon drivers automatically load and ruin your day, create a blacklist file as follows: | |||
{{ | {{file|name=/etc/modprobe.d/radeon.conf|desc=Prevent open source DRM and radeon drivers from loading|body= | ||
blacklist radeon | |||
blacklist drm | |||
}} | |||
==== Custom Kernel ==== | |||
If you are building a custom kernel, rather than blacklisting modules as above, you can simply ensure that the Direct Rendering Manager and in-kernel Radeon drivers are not enabled. If you do build them as modules, you will need to blacklist them as above. Also ensure that the following kernel options are enabled. | |||
{{kernelop|desc= | |||
{| | [*] Enable loadable module support | ||
Processor type and features ---> | |||
[*] MTRR (Memory Type Range Register) support | |||
Bus options (PCI etc.) ---> | |||
[*] PCI Express Port Bus Support | |||
[*] Message Signaled Interrupts (MSI and MSI-X) | |||
Device Drivers ---> | |||
Graphics support ---> | |||
< > Direct Rendering Manager (xFree86 4.1.0 and higher DRI support) ---> | |||
}} | |||
= | {{note|If you need support for AGP cards, enable the following kernel options:}} | ||
{{kernelop|desc= | |||
Device Drivers ---> | |||
Graphics support ---> | |||
<*> /dev/agpgart (AGP Support) ---> | |||
Select an appropriate AGP driver: | |||
<*> AMD Opteron/Athlon64 on-CPU GART support | |||
}} | |||
=== Editing make.conf === | |||
Add the following to your <code>/etc/make.conf</code>: | |||
<console> | <console> | ||
###i## | # ##i##nano /etc/make.conf | ||
VIDEO_CARDS="fglrx" | |||
</console> | </console> | ||
=== Enabling AMD Catalyst Control Center === | |||
Then, add the following to <code>/etc/portage/package.use</code> if you would like to enable support for AMD Catalyst Control Center: | |||
<console> | <console> | ||
###i## | ###i## nano /etc/portage/package.use | ||
x11-drivers/ati-drivers qt4 | |||
</console> | </console> | ||
{{Note|If you are using a desktop or workstation profile, this USE flag will be enabled by default.}} | |||
=== Emerging the package === | |||
If you allready have emerged xorg-server, all you need to install the drivers is running the following command: | |||
<console> | <console> | ||
###i## | ###i## emerge -av --changed-use --deep @world | ||
</console> | </console> | ||
otherwise you may install the drivers with | |||
<console> | <console> | ||
###i## | ###i## emerge -av x11-drivers/ati-drivers | ||
</console> | </console> | ||
Before using the driver, ensure that the "fglrx" module has been loaded -- run {{c|modprobe fglrx}} as root -- it should return with no error. If the module can't be found, run {{c|depmod -a}} as root -- then the modprobe command should work. If you are switching from the open source Radeon driver, then shutting down your desktop and rebooting your system (be sure to disable xdm) may be required to get the new "fglrx" module to load cleanly. | |||
{{ | |||
==== | === Configuring === | ||
Next, set ati-drivers to manage the system's OpenGL and OpenCL implementations. | |||
Doing this is particulary important for desktop environments like GNOME, which use hardware acceleration by default. Not doing this will result in the GNOME display manager not being able to start! | |||
<console> | <console> | ||
###i## | ###i## eselect opengl set ati | ||
###i## eselect opencl set amd | |||
</console> | </console> | ||
Afterwards, run <code>aticonfig</code> to modify the X-server configuration file to work with the ati-drivers: | |||
<console> | <console> | ||
###i## | ###i## aticonfig --initial | ||
</console> | </console> | ||
{{tip|If you would like to have a full-resolution framebuffer with ati-drivers, check out [[uvesafb| uvesafb]]}} | |||
=== Multi-Head Display === | |||
There are a couple of options for setting up a multi-head display. For some systems, all you need to do is plug in your additional monitor, and it will be detected by your desktop environment, and will work. | |||
If your second monitor does not display anything at all, then play around with your X configuration. Try using the following command to generate a new X config: | |||
{{console|body= | |||
# ##i##aticonfig --initial=dual-head | |||
}} | |||
You can use the {{c|--screen-layout={left|right|above|below}}} option to specify the relationship of the second screen to the first. | |||
For more than two heads, or multiple cards, you can use the following approach to generate an appropriate X config. First, list adapters to see what adapters are available: | |||
##### | {{console|body= | ||
# ##i##aticonfig --list-adapters | |||
}} | |||
Now, a variant of one of the following commands to generate an X configuration for your needs: | |||
# | {{console|body= | ||
# ##i##aticonfig --initial --heads=4 --adapter=1 | |||
# ##i##aticonfig --adapter=0,2 --initial | |||
# ##i##aticonfig --adapter=all --initial | |||
# ##i##aticonfig --xinerama=on | |||
}} | |||
One you have your displays enabled so that your mouse pointer can move to all displays, you still may not be able to drag windows to certain monitors. In this situation, each monitor is probably configured as a separate X screen, and you'll need to use the Catalyst Control Center {{c|amdcccle}} GUI configuration tool to tie them together. The Catalyst Control Center is installed when the {{c|qt4}} USE variable is enabled. | |||
Open up a graphical terminal, and become root by typing {{c|su -}} -- your user will need to be in the {{c|wheel}} group to do this: | |||
########## | {{console|body= | ||
$ ##i##su - | |||
Password: ##i##******* | |||
# source /etc/profile | |||
# amdcccle | |||
}} | |||
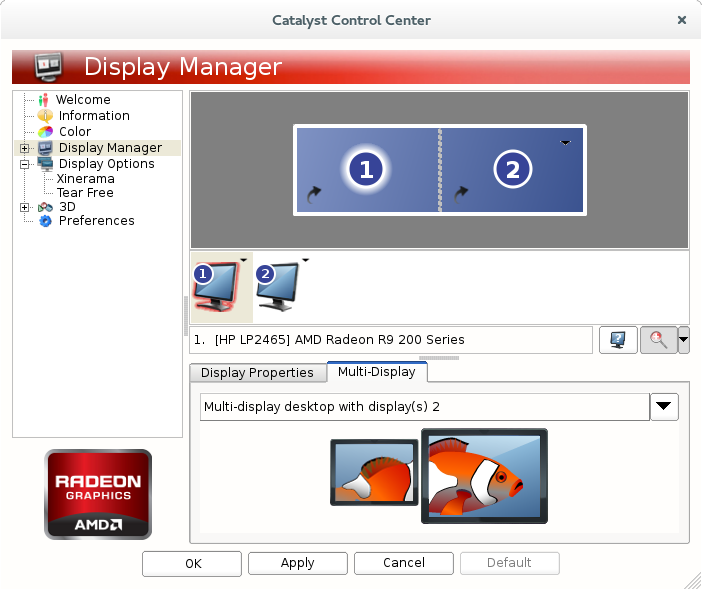
} | [[File:amdcccle.png|class=img-responsive|center]] | ||
Navigate to Display Manager, and choose the option {{c|Multi-display desktop with display(s) X}} for each display. Then, drag and drop the blue displays to arrange them to match how they are arranged in front of you. Click {{c|OK}}. The Catalyst Control Center will tell you that you will need to restart your system for the changes to take effect. Simply log out if you are running {{c|xdm}}, or end your X session, and start it up again. You should now have a fully-functioning multi-head display. | |||
=== Troubleshooting === | |||
==== I am using a HDMI connection, and my monitor's display has a black border around it. ==== | |||
Disable overscan as follows: | |||
############# | <console> | ||
$ ##i##su - | |||
Password: ##i##********* | |||
# ##i##aticonfig --set-pcs-val=MCIL,DigitalHDTVDefaultUnderscan,0 | |||
</console> | |||
You will need to restart your X session for the changes to take effect. If you are using a display manager, logging out and back in again should cause the new settings to be visible. | |||
==== The tabs in Google Chrome are becoming garbled/corrupted ==== | |||
New versions of Google Chrome use hardware acceleration by default which appears to have rendering issues with AMD's drivers. To work around this, disable hardware acceleration in Google Chrome by going to {{c|Settings}}, {{c|Show advanced settings...}} and then uncheck the {{c|Use hardware acceleration when available (requires Chrome restart)}}. Once Chrome is restarted, the rendering problem should be resolved. | |||
==== Compton with backend glx does not work well with ati-drivers ==== | |||
Try running compton with the following switches: | |||
<console> | |||
###i## compton --backend glx --vsync none --paint-on-overlay | |||
</console> | |||
# | |||
</ | |||
[[Category: | [[Category:Video Cards]] | ||
[[Category:First Steps]] | [[Category:First Steps]] | ||
{{EbuildFooter}} | {{EbuildFooter}} | ||
Revision as of 17:42, February 22, 2015

AMD Catalyst Video Drivers
We welcome improvements to this page. To edit this page, Create a Funtoo account. Then log in and then click here to edit this page. See our editing guidelines to becoming a wiki-editing pro.
Version 14.12-r3 and above now include ATI GLESv2 and EGL libraries, which should improve stabilty with GNOME.
x11-drivers/ati-drivers (often referred to as "fglrx", the name of its kernel module) is the proprietary, accelerated driver for AMD (ATI) graphics cards.
Preparing to Install
Default Kernel
If you are using the default kernel -- one like debian-sources that was built automatically, then you'll want to blacklist a few modules to prevent them from loading and interfering with the AMD Catalyst module. To avoid having the open source Radeon drivers automatically load and ruin your day, create a blacklist file as follows:
/etc/modprobe.d/radeon.conf - Prevent open source DRM and radeon drivers from loadingblacklist radeon
blacklist drm
Custom Kernel
If you are building a custom kernel, rather than blacklisting modules as above, you can simply ensure that the Direct Rendering Manager and in-kernel Radeon drivers are not enabled. If you do build them as modules, you will need to blacklist them as above. Also ensure that the following kernel options are enabled.
[*] Enable loadable module support
Processor type and features --->
[*] MTRR (Memory Type Range Register) support
Bus options (PCI etc.) --->
[*] PCI Express Port Bus Support
[*] Message Signaled Interrupts (MSI and MSI-X)
Device Drivers --->
Graphics support --->
< > Direct Rendering Manager (xFree86 4.1.0 and higher DRI support) --->
If you need support for AGP cards, enable the following kernel options:
Device Drivers --->
Graphics support --->
<*> /dev/agpgart (AGP Support) --->
Select an appropriate AGP driver:
<*> AMD Opteron/Athlon64 on-CPU GART support
Editing make.conf
Add the following to your /etc/make.conf:
root # nano /etc/make.conf VIDEO_CARDS="fglrx"
Enabling AMD Catalyst Control Center
Then, add the following to /etc/portage/package.use if you would like to enable support for AMD Catalyst Control Center:
root # nano /etc/portage/package.use x11-drivers/ati-drivers qt4
If you are using a desktop or workstation profile, this USE flag will be enabled by default.
Emerging the package
If you allready have emerged xorg-server, all you need to install the drivers is running the following command:
root # emerge -av --changed-use --deep @world
otherwise you may install the drivers with
root # emerge -av x11-drivers/ati-drivers
Before using the driver, ensure that the "fglrx" module has been loaded -- run modprobe fglrx as root -- it should return with no error. If the module can't be found, run depmod -a as root -- then the modprobe command should work. If you are switching from the open source Radeon driver, then shutting down your desktop and rebooting your system (be sure to disable xdm) may be required to get the new "fglrx" module to load cleanly.
Configuring
Next, set ati-drivers to manage the system's OpenGL and OpenCL implementations. Doing this is particulary important for desktop environments like GNOME, which use hardware acceleration by default. Not doing this will result in the GNOME display manager not being able to start!
root # eselect opengl set ati root # eselect opencl set amd
Afterwards, run aticonfig to modify the X-server configuration file to work with the ati-drivers:
root # aticonfig --initial
If you would like to have a full-resolution framebuffer with ati-drivers, check out uvesafb
Multi-Head Display
There are a couple of options for setting up a multi-head display. For some systems, all you need to do is plug in your additional monitor, and it will be detected by your desktop environment, and will work.
If your second monitor does not display anything at all, then play around with your X configuration. Try using the following command to generate a new X config:
root # aticonfig --initial=dual-head
You can use the right} option to specify the relationship of the second screen to the first.
For more than two heads, or multiple cards, you can use the following approach to generate an appropriate X config. First, list adapters to see what adapters are available:
root # aticonfig --list-adapters
Now, a variant of one of the following commands to generate an X configuration for your needs:
root # aticonfig --initial --heads=4 --adapter=1 root # aticonfig --adapter=0,2 --initial root # aticonfig --adapter=all --initial root # aticonfig --xinerama=on
One you have your displays enabled so that your mouse pointer can move to all displays, you still may not be able to drag windows to certain monitors. In this situation, each monitor is probably configured as a separate X screen, and you'll need to use the Catalyst Control Center amdcccle GUI configuration tool to tie them together. The Catalyst Control Center is installed when the qt4 USE variable is enabled.
Open up a graphical terminal, and become root by typing su - -- your user will need to be in the wheel group to do this:
user $ su - Password: ******* root # source /etc/profile root # amdcccle
Navigate to Display Manager, and choose the option Multi-display desktop with display(s) X for each display. Then, drag and drop the blue displays to arrange them to match how they are arranged in front of you. Click OK. The Catalyst Control Center will tell you that you will need to restart your system for the changes to take effect. Simply log out if you are running xdm, or end your X session, and start it up again. You should now have a fully-functioning multi-head display.
Troubleshooting
I am using a HDMI connection, and my monitor's display has a black border around it.
Disable overscan as follows:
user $ su - Password: ********* root # aticonfig --set-pcs-val=MCIL,DigitalHDTVDefaultUnderscan,0
You will need to restart your X session for the changes to take effect. If you are using a display manager, logging out and back in again should cause the new settings to be visible.
The tabs in Google Chrome are becoming garbled/corrupted
New versions of Google Chrome use hardware acceleration by default which appears to have rendering issues with AMD's drivers. To work around this, disable hardware acceleration in Google Chrome by going to Settings, Show advanced settings... and then uncheck the Use hardware acceleration when available (requires Chrome restart). Once Chrome is restarted, the rendering problem should be resolved.
Compton with backend glx does not work well with ati-drivers
Try running compton with the following switches:
root # compton --backend glx --vsync none --paint-on-overlay